I’m a security paranoid. No tin foil hat, but I do like to stay vigilant. One truth I live by is that no one is below the notice of hackers and other cybersecurity bad actors. If you’re a freelancer or small business owner, never think you’re not on their radar.
Like any other business, hackers have different business models. Some invest in the long con and target high-dollar marks (think: the ransomware attacks on big operators like pipelines and meat-packing plants). But other bad actors have a “spray and pray” model. They work on volume and are happy with lower takes per attack. Hey, if they send out hundreds of thousands of phishing emails and get a 0.1% conversion rate, that’s a win for them. They target people and businesses they believe have poor cybersecurity, like freelancers and small businesses.
But digital and cybersecurity are big, complicated domains. If you’re a freelancer, you’re only paid for your core work, which means you’re less likely to want to spend time (or money) on security. That inherently makes you vulnerable.
So I’ve fought all my security-paranoid instincts and will share my security stack with you.
-
Password manager
-
Multi-factor authentication
-
VPN
-
Endpoint security
-
Encrypted storage
-
Anti-theft protection
-
Backup and restoration
-
Backup devices
A freelancer’s security threat model
A threat model is the process for assessing what you need to protect, where your greatest vulnerabilities lie, and how to prioritize your cybersecurity resources.
Here’s a general picture of my threat model:
-
I use between one and five connected devices for work, so I have a limited number of devices through which hackers can hit me.
-
I don’t have other users and their devices to manage.
-
I often work on public Wi-Fi networks, which is high risk if I don’t take any mitigating security measures.
-
I use local and cloud-based applications, many of which are integrated, which makes my weakest link a weak spot to them all.
-
I store information and files both locally and in the cloud.
-
I store and have access to some information from clients that requires confidentiality because of NDAs and my approach to client care, which means I want to take extra precautions to protect its confidentiality.
-
I don’t collect or store any data that has specific legal protections, such as health data, student data, or any personally identifiable information (PII).
-
My business and livelihood rely 100% on my ability to work and communicate online. Maintaining business continuity in the wake of a cyberattack is a prime objective.
The security stack I have considers all that—and more. If it feels overwhelming to add all of these categories of tools, start with just a couple. Even then, you’ll make yourself a tougher mark to hit.
And note: I’ll mention specific vendors, but I’m not making any product recommendations. Do your due diligence when selecting products.
Security tools to control access
Every security breach includes some sort of unauthorized access. Controlling access should be a significant part of your cybersecurity program.
Password manager (PWM)
Hackers tend to get access using your passwords in two ways.
-
A brute force password-cracking attack figures out your simple passwords. The top ten passwords of 2021 include such stalwarts as “123456” and “password.” Every password on the 2021 Top Ten list can be cracked in less than a minute. C’mon, people. Be better.
-
Through social engineering, hackers can learn enough about you to make educated guesses (hello, middle name). Reusing your passwords increases your vulnerability, especially when you reuse bad passwords.
A password manager generates long, complex passwords that it remembers for you. You only need to remember one passphrase, which is a long string of related words. Using a reputable, secure password manager is also way safer than relying on your browser to store your passwords. Don’t do that. Dashlane and Bitwarden are two popular PWM options.
Untapped value: Use your password manager to store the actual login page too—not just your password. Phishing scams try to get you to click a link to their sophisticated, fake login page. Your password manager can protect you here by not auto-filling a page that doesn’t match exactly the URL it has stored. Some PWMs only do this if you select this option, so make sure you turn on the setting. Here’s what the Dashlane option looks like:
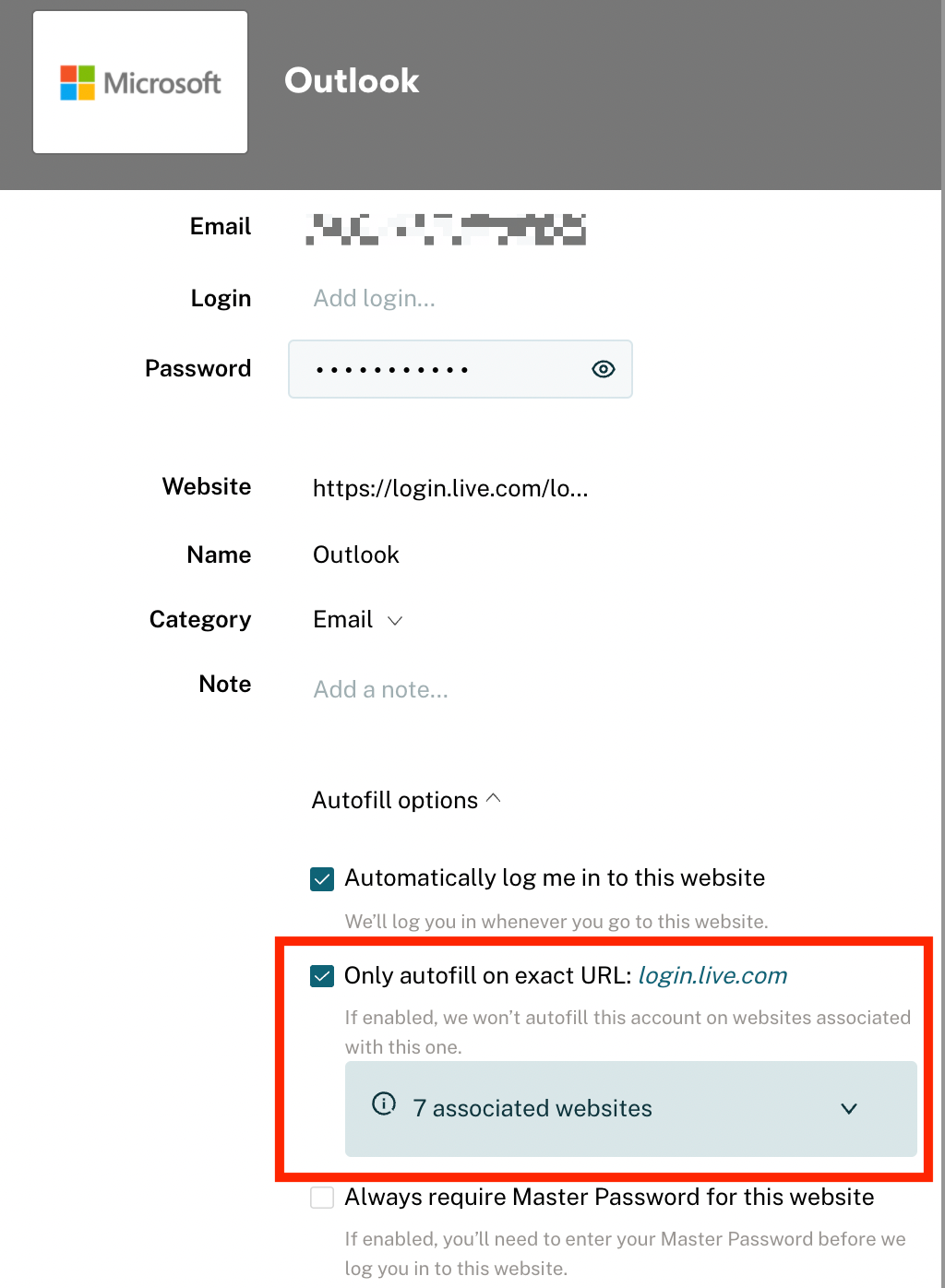
If you’re not a solopreneur: Opt for the business version, which adds a layer of administrative security that manages multi-user access to the password manager.
Multi-factor (MFA) or two-factor (2FA) authentication
When you enable 2FA or MFA, you’re adding an extra layer of access control on top of your passwords. With additional authentication, hackers can’t get into your apps even if they have your password. Authentication can take a few forms, such as a one-time code texted to you, delivery through an authentication app like Authy, or delivery through a separate device.
Biometric authentication is growing in popularity, both for applications and hardware access—and voice authentication seems to be its new frontier. But in my paranoid opinion, voice authentication isn’t mature enough to use for security.
If the extra step of 2FA/MFA bothers you, think strategically about which apps require your highest level of protection. You can usually set it so that the application “trusts” your device for some period of time before you need to go through the 2FA/MFA process again.
Untapped value: You’re probably using apps that already enable 2FA or MFA, so it won’t take much effort to implement. Go into the security settings in all your apps—if 2FA is an option, you should see it there. Here’s what it looks like in your Google account:
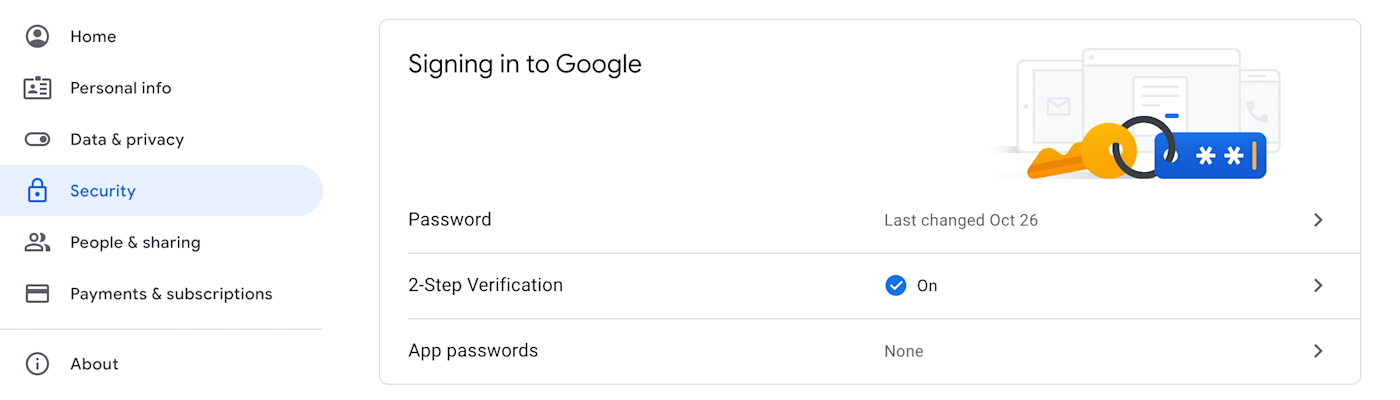
If you’re not a solopreneur: If your organization uses either Google Workspace or Office365, you can set up and require 2FA for all authorized users.
Virtual Private Network (VPN)
Anyone using public Wi-Fi should use a virtual private network (VPN) to do so. VPN software creates a private, encrypted tunnel for your internet traffic, which makes it harder for hackers to intercept. Without it, any hacker at the same airport lounge, coffee shop, or exhibition hall as you can easily monitor your unprotected communications flowing through the public Wi-Fi. A password-protected public Wi-Fi doesn’t mean the network is secure.
Choices in VPNs abound, including ExpressVPN and ProtonVPN, but be sure to review what different vendors let you control—each one offers different settings. No matter which one you choose, connecting to one of the VPN’s servers takes only a click.
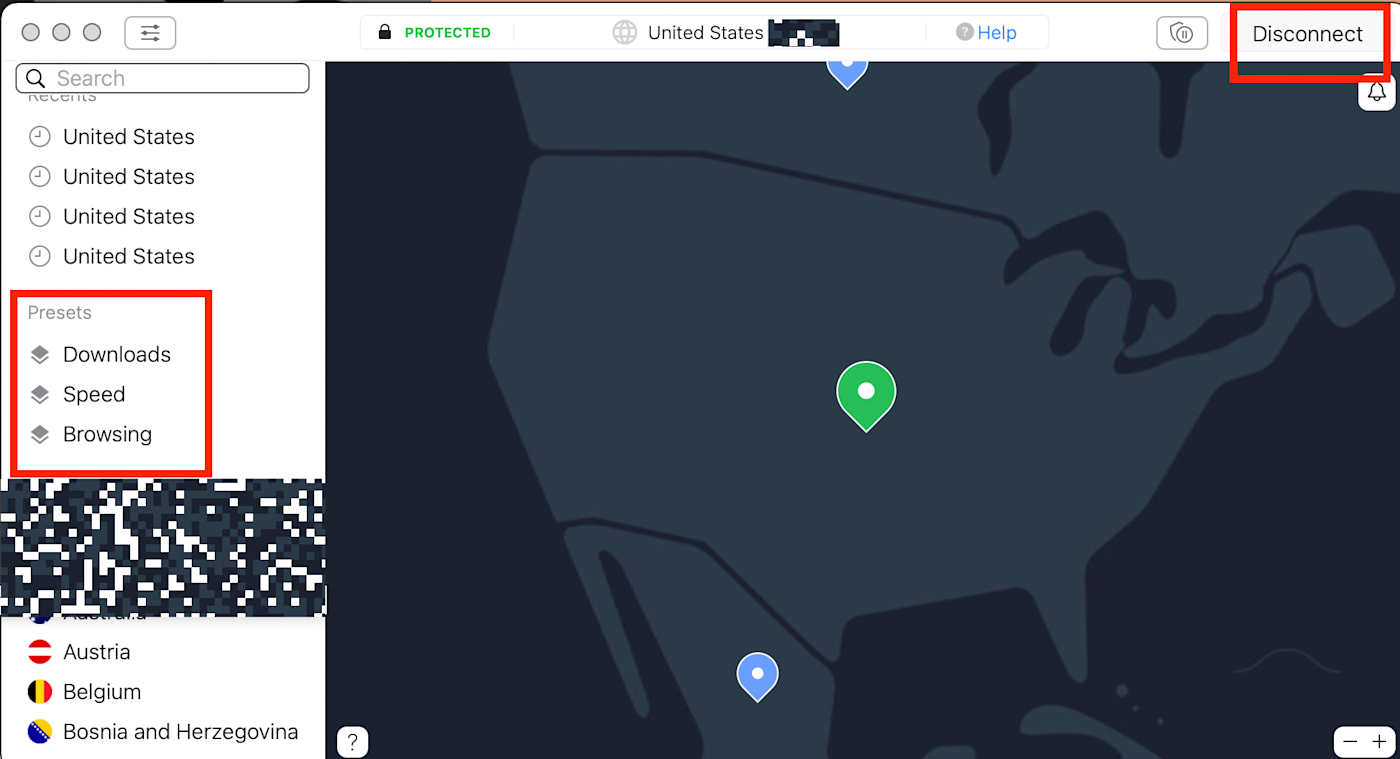
Untapped value: Your private home internet connection may be more secure than public Wi-Fi, but it still presents a common risk, so it’s worth using a VPN at home too. Also: use your VPN software on all your connected devices, not just computers.
If you’re not a solopreneur: If you allow remote work, your VPN security policy should require employees to use VPN on all devices, including personal devices, every time the device connects to business applications. If your business has an on-premise network, look into third-party services that can advise and/or manage installation of VPN hardware.
Endpoint security
I’m using “endpoint security” as an imprecise catch-all term for a suite of security tools that protects you against a wide variety of risks. What they have in common is that they protect your devices from being used as entry points to wreak havoc.
Colloquially, they’re often referred to as anti-virus or anti-malware software, but these are really just two subsets of the protection these security suites provide. If you’re only using a firewall, anti-virus, or anti-malware software, you’re missing out on:
-
Ransomware protection
-
Broader threat detection in communication channels and cloud-based traffic
-
Patch scans that identify software that’s not up-to-date
-
Web filtering or access restriction
These are some of the most commonly used additional protections. I’d suggest checking out the small business security suites from Sophos and Kaspersky since they’re both comprehensive, highly rated, and well-priced (but again—make sure you find the one that’s right for you). Here’s what a dashboard for a single user looks like.

Untapped value: Many of these packages also provide heightened security against hackers taking over your webcam or microphone—a worthwhile protection in our new era of daily video conferencing.
If you’re not a solopreneur: These suites also provide a range of user-management tools, including oversight and blocking of certain websites and applications. Some also offer managed threat detection/managed IT security services, which can be valuable if your small business doesn’t have that expertise in-house.
Encrypted storage
Even though I don’t collect or store data that triggers legal security requirements, I do like having a way to extend a higher level of security to certain documents and information. I do this using an encrypted storage mechanism, separate from my local drive or other cloud-based apps.
You can choose between cloud-based encryption lockers and encrypted external storage, including thumb drives (or both). Whatever medium you choose, you’ll need a complex password as the encryption key. If you lose that, you’ll lose access to everything you’ve encrypted, and you won’t be able to restore it.
Many cloud-based file management and cybersecurity software options include a tool to provide extra security to selected files. For example, Dropbox has Dropbox Vault, and Folder Lock is part of the NewSoftwares’ suite of security solutions.
Untapped value: Your local operating system will let you encrypt files, drives, or your entire machine.
If you’re not a solopreneur: Google Workspace and Office365 also offer encryption options, including encrypting communications. It takes some setup, but it will make sharing files and communicating within and outside of your organization more secure.
Security tools for when things go wrong
As I noted in my threat model, business continuity is a top-priority concern for me. It should be for everyone and every organization, but as a freelance writer who lives and dies by her laptop and internet connection, I feel like my margin for error here is thin.
Anti-theft protection
As a mobile worker, I have to think about what happens if any of my devices are lost or stolen.
Anti-theft software won’t prevent someone from stealing your device, but it gives you tools to limit the damage. It can let you remotely encrypt your device or wipe it clean entirely. If you use it on your phone, you can reset it to factory settings remotely. It also includes location-tracking and other tools to help you recover the device and identify who’s using it (like using the webcam to take pictures of the thief).
Untapped value: If you want the thief to have a bad day too, some tools include activating an alarm on the stolen machine. Other options include pushing out messages to the screen, letting the thief know their picture has been taken or that you know where they are. These tools encourage the thief to abandon your device.
If you’re not a solopreneur: If you provide employees with laptops or other devices, these solutions often include an asset tracking function, and their lockout options are also helpful if you have a separated employee who hasn’t returned their devices.
Backup and restoration
If you’re subject to a ransomware attack, hacker destruction, or a lost machine, you want to have your documents and applications backed up elsewhere. This lets you maintain business continuity while you deal with the attack separately.
Like encryption, you have both hardware and cloud-based backup options. In fact, it’s not a bad idea to use a combination of backup options for redundancy. When selecting a cloud-based backup solution, such as Carbonite or Backupify, make sure you understand what it’s actually backing up and what’s out of scope.
For everyone: Look as closely at how the restoration process will work—not just the backup—when selecting a tool and/or third-party service. The larger your network, the more complicated the restoration. You don’t want to create new security issues as you get systems and your employees back on board. You also don’t want a slow restoration to interfere with operations or client relationships.
Backup devices
If I have a device stolen, lost, or maliciously locked down, I need access to another device without missing a beat. My anti-theft software will help protect the device out of my control, but I need another device to initiate some of those protections. Equally important, I need to get back to work fast. I don’t want to buy a new laptop under a two-hour time constraint.
My secondary devices don’t have my usual suite of applications installed, and I don’t use them otherwise. Secondary devices shouldn’t be in the orbit of your active devices—otherwise they could be at risk as part of the original hacking.
Untapped value: If you’re upgrading, and your current device is in good working order, make that one your backup. Just reset to factory conditions and keep current with operating system updates. Another option is to buy a low-cost laptop for emergencies. It can keep you going while you take your time selecting your new machine.
Cybersecurity is an ongoing process
This is a (mostly) complete picture of my current security stack, but I’m always thinking about new tools to add that will improve my security posture. I keep thinking about it because maintaining strong cybersecurity is a continuous process.
The entry point is identifying your threat model and then continuously reassessing it and your cybersecurity program. Perhaps a tool you have didn’t work as needed in the face of a cyberattack. Unknown risks will appear. As your business evolves, you’ll develop new vulnerabilities. As it grows, you’ll have more resources to invest in cybersecurity.
Using the right tools is vital to building a strong security posture, but tools are only one piece of the puzzle. How you use them—and your other security behaviors—are equally important.
[adsanity_group align=’alignnone’ num_ads=1 num_columns=1 group_ids=’15192′]
Need Any Technology Assistance? Call Pursho @ 0731-6725516




