Significant exposure to third-party risk could cost e-commerce websites millions of dollars in damages and lost revenue, according to a new study by a maker of security products to protect web and mobile apps.
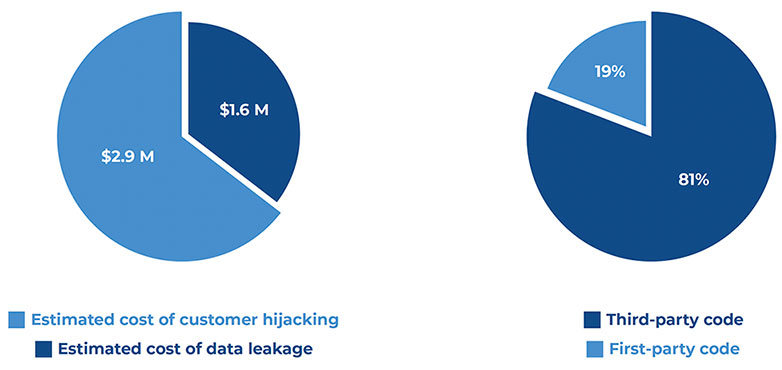
Based on an analysis of two billion user sessions on e-commerce websites, the study by Jscrambler found that third-party services running on the sites attempted to leak 144,000 customer data records, which could have led to US$1.6 million in damages.
Jscrambler researchers also discovered 1.4 million customer hijacking attempts, mostly originating from browser extensions, which could have resulted in $2.9 million in lost revenue.
What’s more, they found that 5% of all customer e-commerce sessions are being actively disturbed by attackers on websites where 81% of the code originated with third parties.
Source: Jscrambler Report – The State of Client-Side Security in E-Commerce
“To keep up with the market pace, companies can’t afford to develop every single component of their e-commerce websites internally,” explained Jscrambler CEO Rui Ribeiro. “Their best option is to use plug-and-play, third-party services to handle everything from analytics to customer service.”
“The problem with this is that it exponentially increases their exposure to third-party risk,” he told the E-Commerce Times. “Every single one of these third-party services provides attackers with an attractive way to breach these websites and get a hold of sensitive user data.”
Pernicious Plugins
Reducing third-party risk is very challenging for organizations, noted Chris Clements vice president of solutions architecture at Cerberus Sentinel, a cybersecurity consulting and penetration testing company in Scottsdale, Ariz.
“Even if the code your team writes is built to be secure, plugins or other software dependencies can inadvertently or maliciously introduce vulnerabilities or data leaks that can expose users to risk,” he told the E-Commerce Times.
“This is especially difficult to verify over time,” he continued. “There are often instances of software upgrades that require dependency upgrades. Ensuring that those downstream changes don’t introduce risk can be challenging.”
He added that client-side issues can be even harder to detect and mitigate. For example, there have been several occurrences where third-party browser plugins or extensions that originally started off with some useful purposes were later sold by the original developer to another organization who then introduced spyware to eavesdrop on users or redirects to send users to different e-commerce sites than they intended.
“Because most browser plugins auto-update,” he explained, “many users are unaware that the malware has been installed on their system.”
Inviting Targets
Even when a third-party vendor is diligent about security, their code can still be compromised. “While many of these third-party vendors do a good job of securing their products, those applications and libraries don’t operate in a vacuum,” said Mike Parkin, a senior technical engineer at Vulcan Cyber, a provider of SaaS for enterprise cyber risk remediation, in Tel Aviv, Israel.
“They can be used in unexpected combinations, which create their own vulnerabilities or be compromised without anyone realizing it,” he told the E-Commerce Times.
“When there is code from multiple vendors in play, and being updated or altered at unpredictable times, it’s a serious challenge for the e-commerce site’s developers to stay ahead of the potential security risks,” he observed.
Third-party applications and libraries, because they are widely distributed, can be an inviting target for attackers, he added. “After all, it’s more efficient to compromise a widely used framework than it is to break into hundreds of separate websites,” he explained.
Website size can influence how susceptible it is to third-party risk, too. “Small sites that are based on open-source software such as WooCommerce / WordPress, CS-Cart, or PrestaShop face different problems than the large commercial sites,” said Brian Martin, vice president of vulnerability intelligence at Risk Based Security, a Flashpoint company.
“Vulnerabilities in open source software and plugins are frequently reported, but the small shop owners typically have no central point of information for vulnerability and remediation information,” he told the E-Commerce Times.
Size Matters
Martin explained that larger e-commerce platforms, such as Shopify, Wix and GoDaddy, have larger security teams that handle a lot of the patching headaches.
“However,” he continued, “they also tend to use a lot of custom code and typically do not issue advisories for vulnerabilities in their platforms, since the customer cannot remediate.”
“This blind spot in vulnerabilities and subsequent breaches may mean their website operators hear about it months after it happens, potentially long after their own customers have been impacted,” he said.
Competitive pressure can also play a role in increasing risk, added Casey Ellis, CTO and founder of Bugcrowd, a crowdsourced bug bounty platform. “The e-commerce space is particularly prone to hyper-competitiveness,” he told the E-Commerce Times. “That sort of environment rewards hasty execution, and haste is the natural enemy of security.”
While third-party risk is something all websites face, it can be a greater threat to e-commerce sites. “Since actual PII and payment data are a necessary function of interacting with an e-commerce website, vulnerabilities which are common but often fairly benign — such as reflected cross-site scripting — can have an outsized impact on an e-commerce site,” Ellis noted.
Surprising Culprits
Jscrambler’s report also found a variety of third-party scripts running on the websites monitored for the study that were completely unknown to security teams. This can happen both because other teams inside the company are adding scripts without any awareness of security teams and because third-party scripts can start adding fourth parties to the website, it explained.
But it’s not only unknown scripts that are a cause for concern, the report added. Its analysis highlights that a significant portion of the thousands of attempted data leaks originated from scripts that were known to the security teams and assumed to be trustworthy.
“One might expect that these data leaks would originate from unknown sources, but we actually found that several of the data leak attempts we detected came from vendors that were already known by the companies that were using them,” Robeiro said.
“These findings really illustrate how dynamic all these services are and how quickly a benign third-party service can become infected and leak sensitive data with no awareness from the victim websites,” he continued.
“It’s no surprise to see security standards such as PCI DSS now requiring e-commerce websites to keep an updated inventory of all of their website’s scripts and monitor in real-time for the addition of any malicious code such as e-commerce skimming code,” he added.




