Having a key for your front door doesn’t matter if you never lock it. That’s why the right mindset and behaviors are crucial for making the most of your digital security stack.
I’m sharing seven ways I take responsibility for the “human element” to make the most of my security tools and strengthen my security posture. This isn’t a complete list of all the actions you should take, but it’s all easy stuff that you can do almost immediately to improve your security.
-
Be “politely paranoid”
-
Do your due diligence before you click
-
Create strong passphrases
-
Have backup redundancy for access codes
-
Review which apps have access to other apps
-
Know which devices are logged in to your accounts
-
Keep your OS and software up to date
1. Be “politely paranoid”
A lot of hacking starts with a simple interaction: a phone call, an email, or even an in-person conversation. I take a hesitant—some would say “mildly suspicious”—approach to calls and emails from unknown sources. Rachel Tobac, white hat hacker and CEO of SocialProof Security, puts it in much nicer terms. She advocates we be “politely paranoid.”
Being politely paranoid means starting with an awareness that an interaction could be an attack, so you bring a healthy wariness to the interaction.
If someone calls saying they’re from your bank and need your password—I think we all know not to do that now. But hackers are cleverer than that today and can make good use of a wide variety of information, even if it doesn’t seem personal. Did you get a call from the “help desk” and they need to know what OS version you’re running on your computer? Seems tame enough, but that’s really valuable information to a hacker. Taking a stance of polite paranoia can help you suss out these interactions before you give away any information.
Social engineering hackers already know a good deal about you before they make contact (the more you publicly share online, the more they know). Tobac explains that bad actors use what you share to personalize a scenario designed to motivate you to give up the information they really want to complete their hack.
My approach may veer into the unhealthy type of paranoid. If I don’t recognize a phone number, I don’t answer the call. If they leave a message, I do some independent research and decide if I’ll call back. I understand this may not be an option for everyone—or one you want to take.
If you do engage in the interaction, don’t offer information. Be the one asking the questions. They’ll often use emotional or urgency triggers to squeeze information out of you right now before you have a chance to think about whether sharing is a good choice. So slow down the conversation. Ask them for the information you need to resolve whatever the crisis is so you can address it outside of that conversation. If it’s legit, you’ll get the information you need and can end the conversation without sharing anything with them. If it’s not, they’ll keep pushing for information from you (red flag) or end the conversation.
2. Extend your polite paranoia to deciding whether to click through an email
This is tough because never clicking through an email isn’t an option—even for a security paranoid like me. However, emails with links can present a high risk. Sometimes the click is the problem, and it will download bad stuff to your machine. Sometimes the click takes you to a well-designed, bogus landing page that mimics a site you do know. The hacker’s goal is to get you to enter personal information or login credentials into their bogus site.
I’m comfortable clicking through emails from known contacts. But of course, some email hacks start by spoofing the email to make it look like it’s from a known organization or contact. That’s where staying politely paranoid is helpful.
If something feels “off” about the email, don’t ignore your spidey senses just because you’re afraid of looking paranoid or low-tech. Someone I know got an email from her boss’s personal Gmail, instead of the company email. That was unusual. She was smart and sent him a Slack message to confirm that the email was really from him. It was, so she went ahead and clicked. A simple check can save a ton of hurt.
Spoofed LinkedIn connection request emails were an issue once. When I see one in my inbox, I still won’t click it. I go to LinkedIn. If the connection request is authentic, I can act on it there. I’ve had at least two instances the past year where a LinkedIn email notification about connection requests didn’t show up in the app. Who knows—perhaps they changed their minds and withdrew their requests. Perhaps.
So stay aware that hackers may spoof known contacts or organizations. Look for red flags, especially from emails purporting to be from organizations that are good targets, like financial institutions or loyalty programs.
When I get emails from unknown people, I look those people up online outside the email. If the email content aligns with what I see online, I still might not click on the link. I’ll either reply or delete the email. If the content doesn’t align—I’ll delete or mark as spam.
3. Create strong passphrases that you can remember without writing down
Ideally, you’re using a password manager. It will create long, complicated, hard-to-hack passwords for your apps that you don’t need to remember. You just need to create one strong passphrase that you can remember to access everything.
The conventional wisdom for creating a strong passphrase is to string together four random words. My preference is to create a string of word associations that make sense to me. Don’t use your favorite sports teams or movies as a starting point. What’s on your to-do list the day you’re creating the passphrase? You have to mow the lawn or shovel snow? Start with “lawn,” “shovel,” or “snow” and free-associate from there. (I don’t actually mow lawns or shovel snow, but I’m not going to share my trigger words with you. This is me being politely paranoid.)
If the word association lends itself to adding numbers or symbols—even better.
4. Have backup redundancy for application backup codes
Ah, those strings of complicated text we’re told to keep in a safe place because it’s the only way we’ll be able to access apps that hold our highly sensitive information. I’ve been burned by this one. If you don’t know where you keep your backup codes when you need them—there’s nothing you can do.
Having learned the hard way, I now have two options to make sure I can always access my backup codes, if needed:
-
I add the backup codes to the app’s record in my password manager. Most password managers include a notes field for each app record for additional information. They also typically let you create secure notes, separate from a password record. You need to use your passphrase to access the secure note.
-
I also store them as files in an encryption locker or secure, external drive. The password manager provides quicker access, but in case something happens to my password manager access or it gets corrupted, I still have them.
5. Know which apps have access to other apps
5 things you should automate today
Integrating apps saves time, reduces human error, and lets you focus on more important work. I’m all for it. But you do want to take inventory regularly and revoke permissions for unnecessary apps.
I’m not a huge user of Twitter. I got a bit lazy with this one and hadn’t looked at its integrations in a while. Checking for this article, I found I had given at least 20 apps access to my Twitter account. I couldn’t even recognize most of them. Upon investigation, I see that some of them aren’t even around anymore.
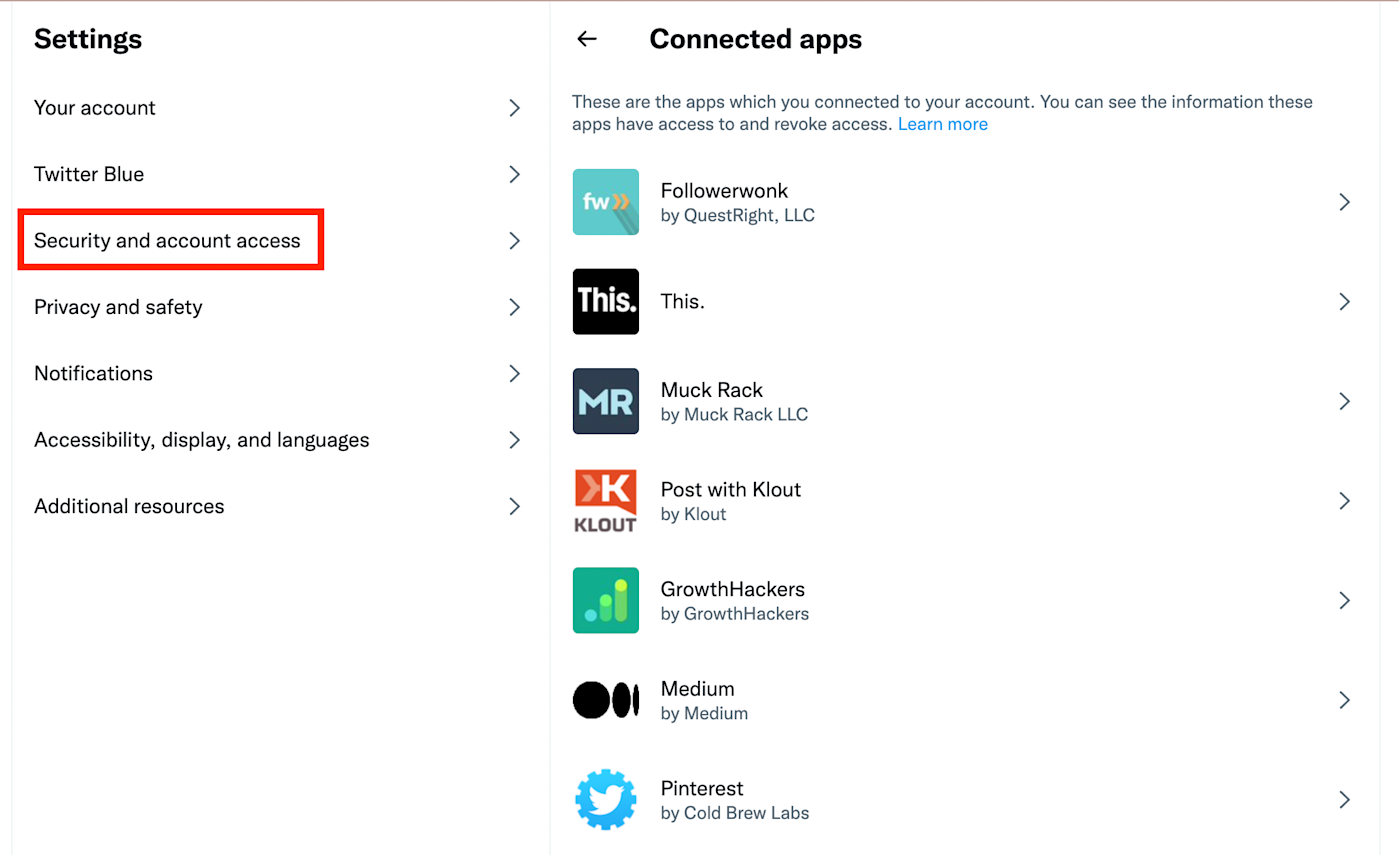
Time to clean house and remove access.
6. Know which devices are logged in to your accounts
Everyone has at least two devices—plenty of us probably use more. Many popular applications, like Google and Netflix, show you which devices are currently logged in to the account and provide a device login history.
When you go to your Google account admin page, click the Security option. From there, you’ll see these options to manage both device logins and third-party access.
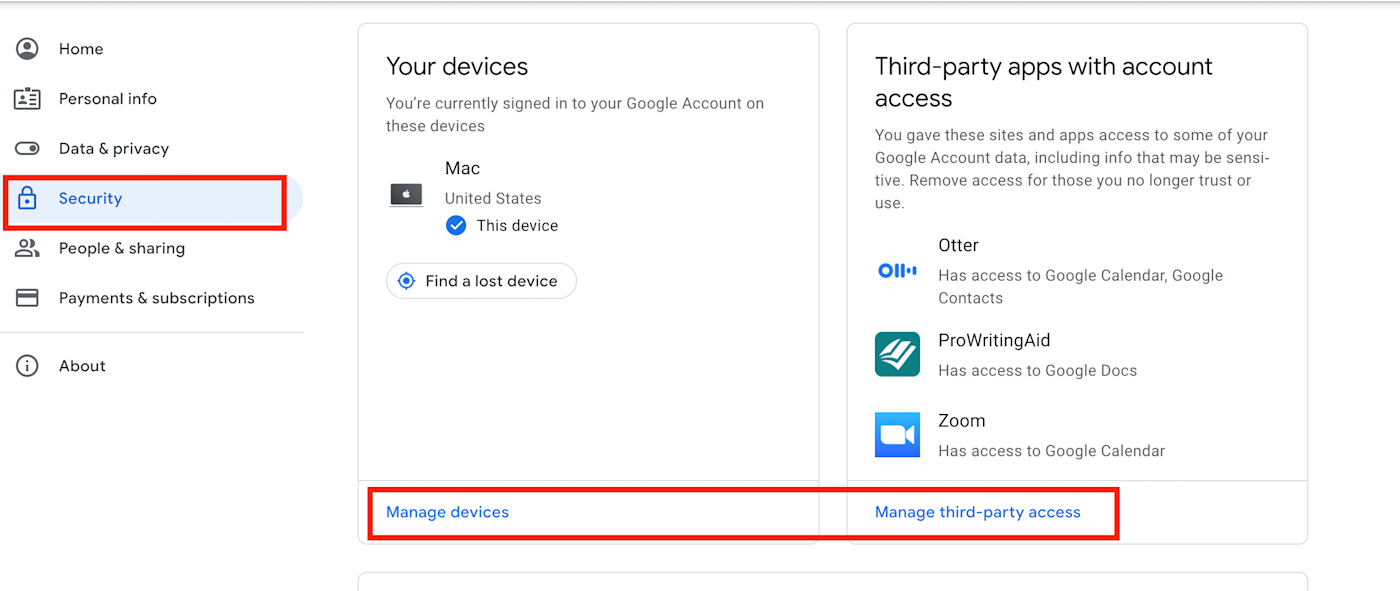
I not only check regularly for unknown devices; every so often, I also use the option to log out of all devices. Even if I don’t see any unusual activity, I like having a clean slate. Some applications make this easier than others.
If you have a Google account, select Manage devices under Your devices from that same security page. If you don’t recognize a device or it no longer needs access, click on the dot stack in the upper right-hand corner to log out. You’ll have to change your password.
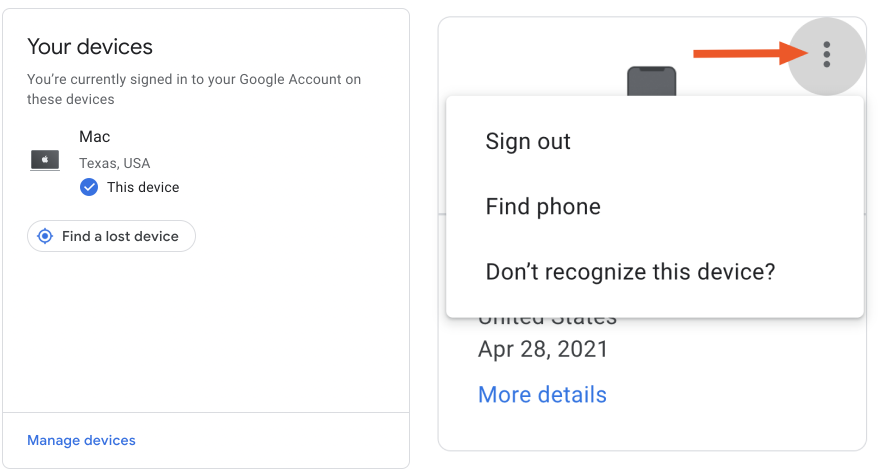
Note that logging out of Google on all devices does not log your Google account out of the third-party apps that have access. You need to revoke permissions for any app you no longer want to have access to your Google account. To do that, click Manage third-party access on the security page.
If you’re not familiar with the security settings on the apps you use, take some time and start looking around.
7. Keep your operating system and software up to date
There are hackers out there exploiting known bugs that were patched up almost 10 years ago. How? Because there are people who don’t keep up with their OS and software patch and version updates.
You can set your operating system and most applications to auto-update when a new version and patch come out. I don’t like giving up that much control to the machines. Instead, I opt for update notifications. If I can’t run it immediately, I’ll schedule it to run later that day.
If you feel like there’s reason to be wary of the update itself (cough, cough: iOS), one option is to follow the tech news after the patch or new version is released to see how things shake out before updating. That’s a personal judgment call.
Awareness and consistency strengthen your defense
This clearly isn’t a complete list of everything needed to reinforce online defenses. But it’s a good starting place to turn security behaviors into habits.
These steps are based on security principles of consistency, vigilance, and privacy. In other words, know your tech environment as it grows, and keep it current to what you need—and no more.
A popular cyber security principle is “least privilege”: limiting access and authority only to what’s needed. With these steps, I apply the principle of least privilege to my own environment. I try to keep the devices and applications in my environment limited and keep information close to the vest. I make deliberate decisions whether to show trust in an interaction or to be more circumspect.
You’re never too small to be a target. Proceed as if you are one.
[adsanity_group align=’alignnone’ num_ads=1 num_columns=1 group_ids=’15192′]
Need Any Technology Assistance? Call Pursho @ 0731-6725516







