Highlights:
- In video meetings, end-to-end encryption (E2EE) prevents any third parties—including the service provider—from accessing or eavesdropping on conversations.
- Data is encrypted on the sender’s machine and relayed directly through the service provider. Only the receiver can decrypt the key.
- This adds an extra layer to mitigate risks and ensure total privacy in a video meeting.
- RingCentral users can now use Dynamic End-to-End Encryption. Simply select the option when scheduling a meeting.
This is the second blog of our RingCentral MVP™ security series. Check out the previous post where we highlight the four building blocks of security in RingCentral MVP.
Video conferencing has become a key business enabler for teams and companies everywhere—especially after the massive shift to remote work. And it’s here to stay. Businesses are moving increasingly hybrid, and video will be a big part of that strategy.
But now that video meetings (and other cloud-based communications) are vital to our work lives, cybersecurity has only become more challenging. Not only are we meeting virtually more than ever, we’re also dialing in from places that can expose users and their companies to threats.

Which brings us to encryption—an important way for businesses to protect their sensitive information from hacks. Encryption makes information unreadable, and only an encryption key can decipher it. Whoever has access to the encryption key has access to the contents.
So what about end-to-end encryption (E2EE)? What exactly is it? What does it protect against? And who owns the encryption and decryption keys in E2EE? Let’s look at the basics.
End-to-end encryption, explained
End-to-end encryption (E2EE) in video conferencing encrypts every bit of information in a meeting so that no third parties can intercept and tamper with the meeting contents—not even the video provider itself.
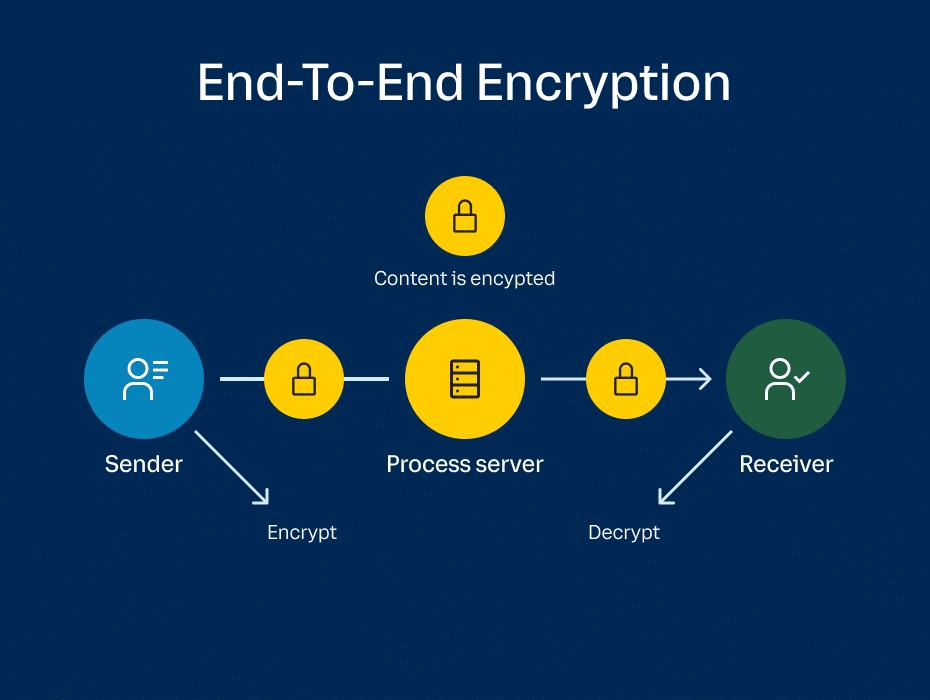
Encryption keys are generated from the sender’s device in a way that only recipient devices (fellow meeting participants) can decrypt them. The data relays directly through the service provider’s network in encrypted form, bypassing any chance of eavesdroppers accessing the cryptographic keys. That includes the video and audio streams, messages, and files shared throughout the meeting.
In a nutshell, E2EE ensures that your meeting contents are completely protected in the event of an attack. Even if your video conferencing provider’s network or servers are compromised, hackers can’t gain access to the encrypted data.
End-to-end vs data-in-transit
Data-in-transit encryption works a bit differently than E2EE. With data-in-transit—the encryption method used in most video meetings—information is encrypted on the sender’s device and decrypted by the video provider. The provider has access to all of the data before encrypting it again and transmitting it to the receiver.
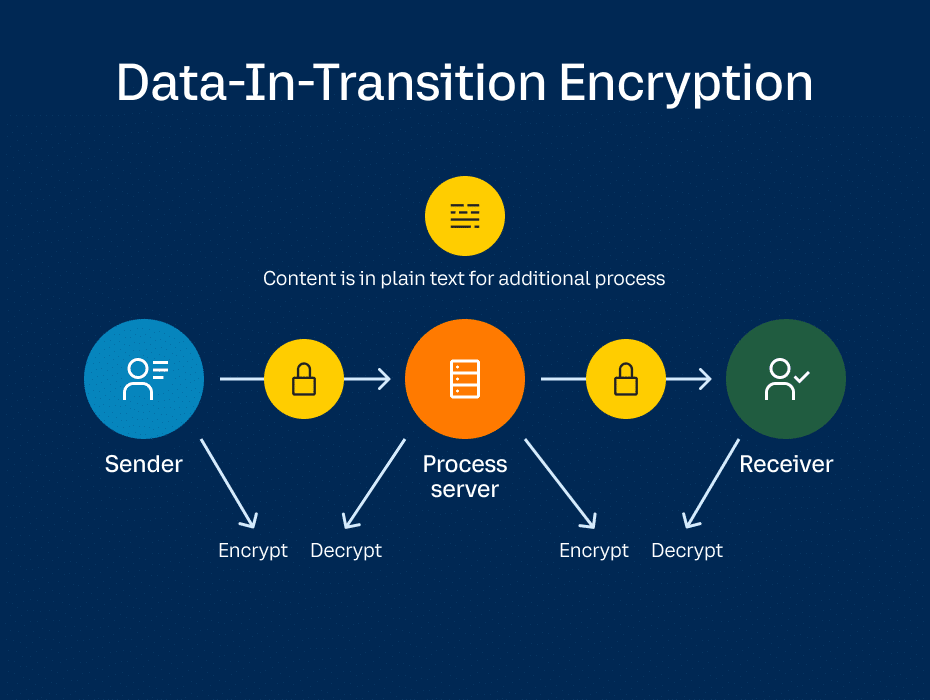
Since the encryption keys are generated on the provider’s end, data-in-transit allows providers to offer several video conferencing features. For example, users have access to cloud recording, live transcripts, and PSTN dial-in/dial-out capabilities simply because the provider has full access to the information.
Data-in-transit encryption:
- Sender encrypts the information.
- Provider decrypts it.
- Provider encrypts it again.
- Receiver decrypts it.
End-to-end encryption:
- Sender encrypts the information.
- Information travels through servers uninterrupted.
- Receiver decrypts it.
In E2EE, encryption keys are generated by the sender instead of the provider and transmitted directly to the receiver. No one but the participants in the same meeting can access the information.
The tradeoff with E2EE is that since the video provider has no access to the meeting contents, it can’t provide services like cloud storage, live transcripts, and dial-in/dial-out.
Why E2EE matters
Data-in-transit encryption protects video meetings from man-in-the-middle (MITM) attacks, where a hacker intercepts decryption keys between two parties.
But for video meetings where you want enhanced privacy and data security, E2EE adds an extra layer to mitigate risk and shield sensitive information. Here’s how:
- Protection against security breaches in your provider’s network: With E2EE, data is encrypted the entire time it traverses the provider’s network. Because only participants have the decryption key, data cannot be unencrypted during its journey, even if the provider experiences a breach.
- Protection from administrator attacks: Administrator accounts are another attractive target for hackers. With E2EE, administrator accounts don’t have access to encryption keys—only participants do—closing yet another potential vulnerability.
- The highest guarantee of privacy and confidentiality: Because the keys required to decrypt meeting data exist only on participants’ machines, there is no way for a third party to intercept and decrypt it at any point.
Which is best for you?
Remember that there are pros and cons to both end-to-end and data-in-transit encryption. With E2EE, you have total confidentiality and peace of mind that your video meeting is fully private—but value-added services like live transcripts and cloud recording won’t be available.
With data-in-transit, you have access to those services and protection from eavesdroppers while your communications are en route from sender to receiver. But to ensure maximum confidentiality in your video meeting, E2EE is the way to go.
Of course, how you approach each video meeting will be different. For example, a monthly all-hands meeting might benefit from services like cloud recording—thus you would choose data-in-transit encryption. A meeting to discuss sensitive financial or legal information, however, requires total privacy—and you would choose end-to-end encryption.
Go ahead. Try it out.
Last month, we announced the launch of Dynamic End-to-End Encryption, which is now available to all RingCentral users (currently in open beta).
When you choose to activate end-to-end encryption, we won’t have any access to your meeting contents. At the same time, video meeting services will be disabled while E2EE is on. Hosts can toggle on E2EE when scheduling a meeting through the RingCentral app or RingCentral Scheduler for Outlook.
Learn more about using end-to-end encryption in our knowledge base article and FAQ.
Looking For Startup Consultants ?
Call Pursho @ 0731-6725516
Telegram Group One Must Follow :
For Startups: https://t.me/daily_business_reads